
7 Phishing Awareness Email To Employees 2023 Phishing Awareness Email Templates For Employees
The information you give helps fight scammers. If you got a phishing email, forward it to the Anti-Phishing Working Group at [email protected]. If you got a phishing text message, forward it to SPAM (7726). Report the phishing attempt to the FTC at ReportFraud.ftc.gov. Search Terms.
Phishing Scams How to Spot Them and Stop Them CSC
From the Malwarebytes Forums, go to the Research Center. In the Research Center, click the subforum that best describes the file or website you are submitting. To see guidelines for each subforum, click the pinned topic titled Purpose of this forum. Click Start new topic. Create and submit your new topic. Zip the file.
Things to know about Phishing attacks DEV Community
URL Phishing Definition. URL phishing is a form of phishing attack that is initiated by sending a malicious email to an unsuspecting victim that contains a URL to a fake website, instructing them to visit it. URL phishing can be used for many purposes, from stealing bank account information to installing malware on a device.

What Is Phishing Attack Definition Types And How To Prevent It Images and Photos finder
Laporkan Laman Phishing. Terima kasih telah membantu kami mengamankan web dari situs phishing. Jika Anda yakin telah membuka laman yang dirancang menyerupai laman lain dalam upaya memperoleh informasi pribadi pengguna, lengkapi formulir di bawah ini untuk melaporkan halaman tersebut kepada tim Penelusuran Aman Google.
20 types of phishing attacks + phishing examples Norton
Email attack is the preferred method for many hackers -- a cybercriminal sends an email that attempts to fraudulently acquire the recipient's personal information. A phishing email might include an attachment or a link or request personal information. The email may appear to be legitimate communication from your bank, phone company, a store.

Phishing Office of Information Security Washington University in St. Louis
Phishing is a crime that has been plaguing users on the Internet for years. By reporting any suspicious contact to the proper organizations, you may have a part in helping to cut down on such unlawful activities in the future.

What is phishing? How to recognize and report phishing emails? ioSENTRIX
1. Call companies where fraud occurred. If you accidentally provided personal information and become a victim of identity theft, you should immediately contact the businesses where the fraud occurred. Ask to speak to the company's Fraud Department and report the fraud. Ask the company to freeze your accounts.

Phishing simulation reveals 70 of workers who clicked on malicious link
Send a Report to Google. If you believe you've encountered an unsafe page where Google Safe Browsing should be displaying a warning but isn't, or a legitimate page where Safe Browsing is incorrectly displaying a warning, please complete the following form to notify the Safe Browsing team. Learn more.

How to protect against phishing 18 tips for spotting a scam
If you know these conditions, select them below. Phish Report analyses over 50,000 phishing sites every day. See how it works →. Detect, disrupt, and deter consumer phishing attacks. Phish Report gives your team the same capabilities as leading brand protection services.

What is phishing? How to recognize and report phishing emails? ioSENTRIX
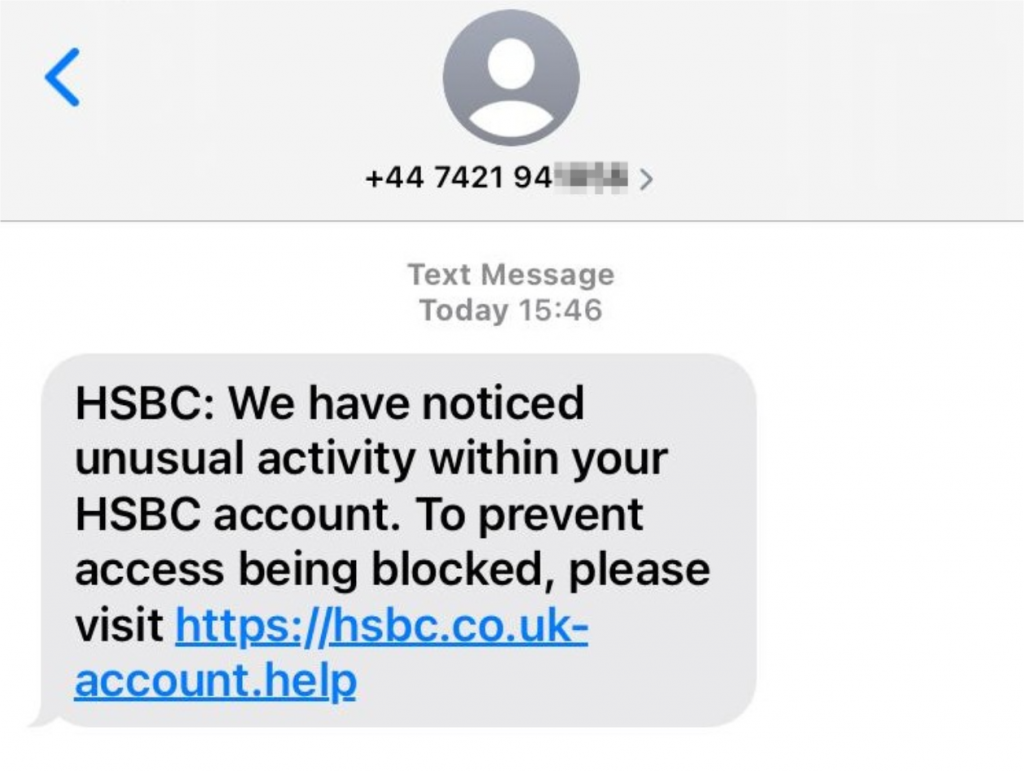
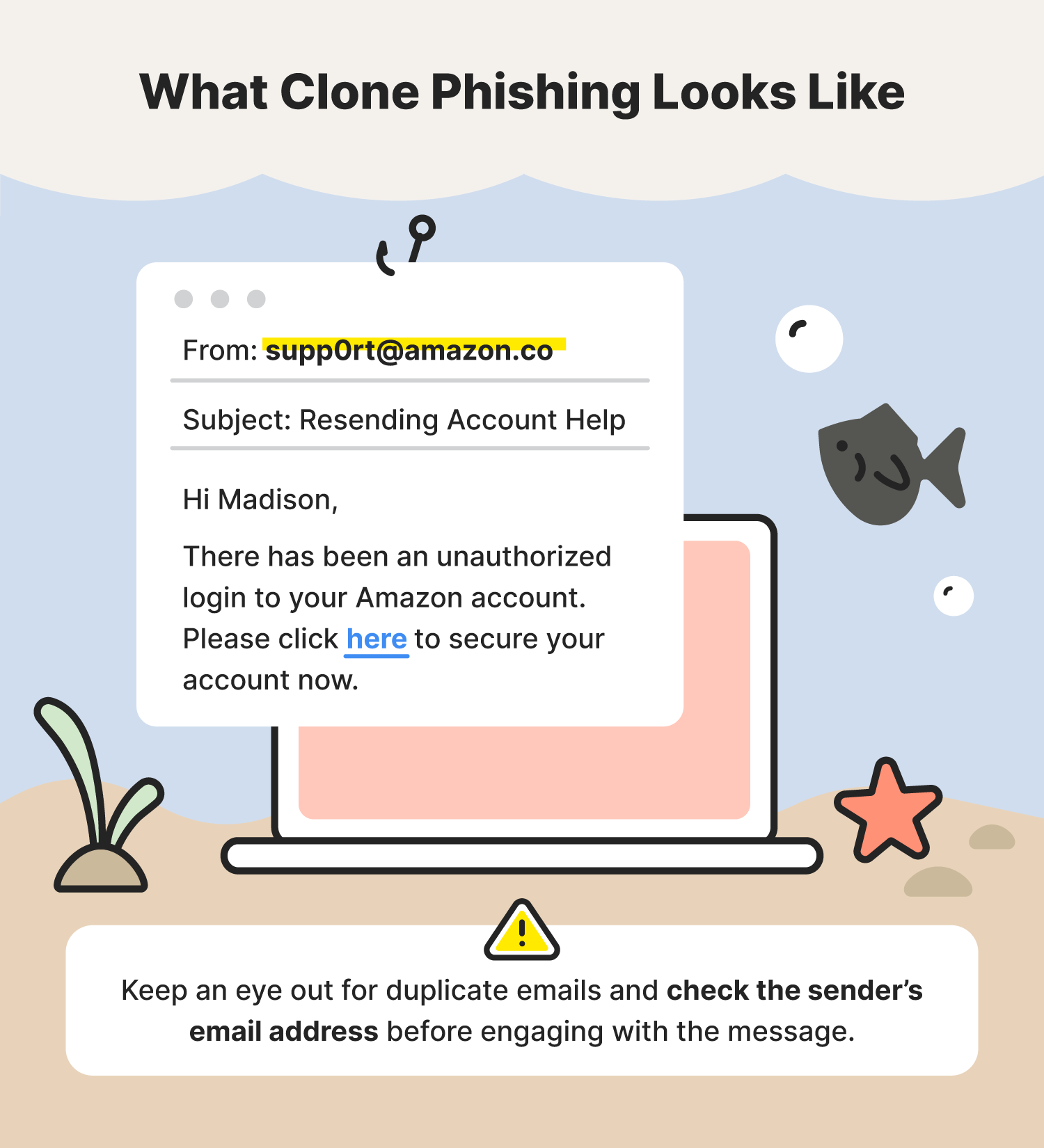
Spoofing is when someone disguises an email address, sender name, phone number, or website URL—often just by changing one letter, symbol, or number—to convince you that you are interacting.

7 Top Email Phishing Scams
Phishing is a cyberthreat in which scammers try to lure sensitive information or data from you by disguising themselves as a trustworthy source. They do this using a variety of communication methods, including email, Google Chat, text messages, phone calls, and more. No matter which method scammers use, they want your personal information so.

Phishing Attacks and How to Protect Against Them Office of the Victorian Information Commissioner
Forward phishing emails to [email protected] (an address used by the Anti-Phishing Working Group, which includes ISPs, security vendors, financial institutions, and law enforcement agencies). Let the company or person that was impersonated know about the phishing scheme. And report it to the FTC at FTC.gov/Complaint.
How to Spot a Phishing Website
You can use EasyDMARC's phishing link checker by copying and pasting the URL into the search bar and clicking "Enter." You'll receive information about each link separately in a few seconds. You can also paste text containing links into the box. The tool checks for phishing URLs, simultaneously detecting and analyzing up to 20 links.
Tech Byte 4 UReport a Suspected Phishing page or a mail containing Phishing page's link
Some phishing links lead to websites that trigger an automatic download of malicious software (i.e., malware). If executed, this malware can perform a variety of different actions, such as data theft or hijacking a victim's online identity. The implications of malware are severe and cannot be understated. 2.

How to Purify Your Device After Clicking a Phishing Link
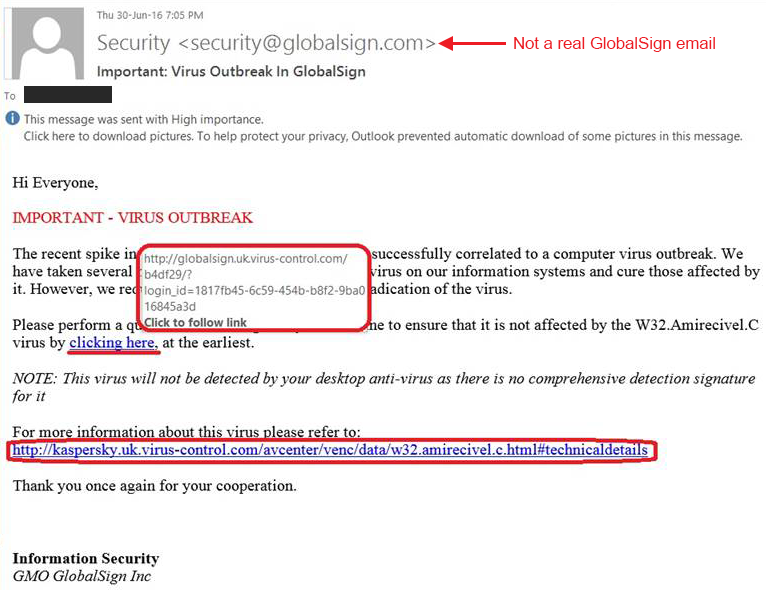
There are two parts to a link: The words describing the link (the part you see) and the URL. If you're on a computer, hover over the link and find out its real destination. If it doesn't match the link displayed, assume it's unsafe and don't click it. This is an easy, effective way of spotting phishing threats.

10 Top Tips How to Detect Phishing Scams SecurityHQ
The tools your team need to combat brand impersonation. Phish Report gives you the same capabilities as leading brand protection services and guides you through the takedown process. Hosting provider analysis. Get verified abuse reporting steps for every provider involved in hosting a phishing site. Step-by-step response.